Xcode 16 Di Lengkapi Dengan AI Buat Coding Aplikasi Lebih Mudah
Morrissey Technology – Meski tidak masuk dalam pengumuman utama, Apple memperkenalkan sejumlah alat dan sumber daya baru untuk pengembang di hari pertama WWDC 2024. Ini termasuk penyempurnaan Xcode 16, Swift dan API baru yang dapat digunakan pengembang untuk membangun aplikasi.
“Apple berkomitmen untuk menyediakan teknologi dan sumber daya mutakhir bagi para pengembang di mana pun untuk membangun aplikasi yang luar biasa,” kata Susan Prescott, Vice President, Worldwide Developer Relations Apple.
“Dengan inovasi yang cermat di balik Xcode 16 dan API platform terbaru, kami telah menciptakan alat terbaik bagi para pengembang untuk membuat aplikasi yang luar biasa. Kami tidak sabar untuk melihat apa yang akan mereka ciptakan selanjutnya.”
Xcode 16
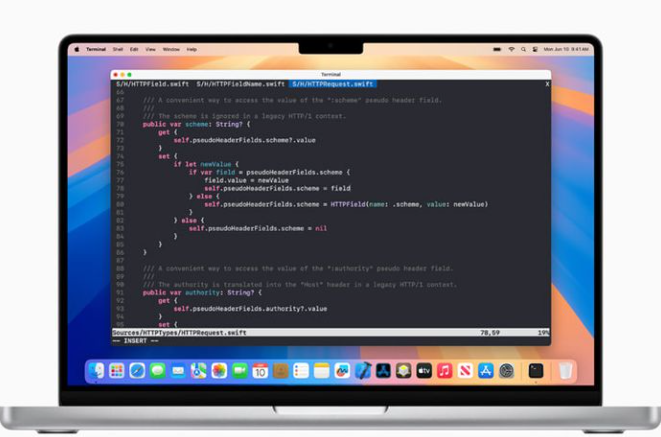
Xcode 16 menawarkan fitur dan peningkatan performa yang memberdayakan pengembang untuk membangun aplikasi lebih cepat dibandingkan sebelumnya. Apple menyematkan Swift Assist dan penyelesaian kode prediktif. Mesin penyelesaian kode prediktif baru di Xcode menggunakan model unik yang dilatih khusus untuk Swift dan Apple SDK, yang dapat menyarankan pengembang kode yang dibutuhkan. Pelengkapan kode didukung sepenuhnya oleh Apple Silicon dan peningkatan pembelajaran mesin di macOS Sequoia, dan berjalan secara lokal di perangkat pengembang
Swift Assist terintegrasi dengan mulus ke dalam Xcode Scatter Hitam , dan mengetahui kit pengembangan perangkat lunak (SDK) terbaru dan fitur bahasa Swift, sehingga pengembang akan selalu mendapatkan fitur kode terbaru yang menyatu sempurna dengan proyek mereka. Swift Assist menggunakan model canggih yang berjalan di cloud, tetapi dibuat dengan mempertimbangkan privasi dan keamanan. Kode pengembang hanya digunakan untuk memproses permintaan dan tidak pernah disimpan di server, dan Apple tidak akan menggunakannya untuk melatih model pembelajaran mesin. Pratinjau Xcode kini menawarkan arsitektur penautan dinamis baru yang menggunakan artefak build yang sama untuk pratinjau dan eksekusi kode. Pengembang sekarang juga dapat melokalkan dan menguji kebijakan privasi, perjanjian lisensi, dan nama tampilan grup langganan aplikasi mereka.
Swift 6
WWDC24 menandai ulang tahun ke-10 Swift. Saat ini, hampir 1 juta aplikasi menggunakan Swift, dan digunakan di seluruh tumpukan perangkat lunak Apple. Swift 6 memperkenalkan fitur keselamatan data-race pada saat kompilasi, yang mampu mendiagnosis akses serentak ke memori di seluruh proyek pengembang saat kode sedang dikompilasi. Hal ini memungkinkan kesalahan terdeteksi dan diperbaiki dengan perubahan minimal pada seluruh basis kode, meningkatkan keamanan dan pemeliharaan kode untuk masa mendatang.
Melanjutkan ekspansinya, sebuah organisasi GitHub baru yang didedikasikan untuk Swift akan menjadi tuan rumah sejumlah proyek penting untuk ekosistem Swift – termasuk kompilator Swift, Foundation, dan pustaka utama lainnya. Kerangka kerja Swift Testing lintas platform yang baru menawarkan API ekspresif kepada pengembang yang memudahkan penulisan pengujian. Kerangka ini bersifat lintas platform dan mudah dipelajari, sehingga pengembang dapat menggunakannya untuk menulis pengujian untuk berbagai platform dan domain.
Kerangka kerja ini juga mencakup sistem penandaan yang fleksibel untuk membantu pengembang mengatur pengujian dan rencana pengujian mereka. Pengujian Swift dirancang untuk banyak kasus penggunaan Swift, mulai dari aplikasi hingga server.
Game Porting 2
Game Porting Toolkit 2 mempermudah pengembang menghadirkan game ke ke Mac, serta iPhone dan iPad. Selain itu dengan peningkatan kompatibilitas dengan game Windows, alat debug shader baru yang canggih, dan pembaruan pada Xcode yang memungkinkan pengembang menyatukan kode game dan shader mereka di berbagai perangkat, alhasil membuat game di perangkat Apple menjadi semakin mudah.
Pengumuman di WWDC 2024 juga mencakup API baru, peningkatan TestFlight untuk keterlibatan penguji yang lebih baik, dan fitur baru untuk App Store yang membantu penemuan dan monetisasi aplikasi. App Store Connect telah diperbarui dengan antarmuka baru dan pembuatan aset pemasaran untuk pengembang. VisionOS 2 menawarkan API baru untuk menciptakan pengalaman spasial, termasuk API volumetrik dan TabletopKit untuk menghubungkan aplikasi ke permukaan datar. RealityKittelah diperbarui untuk mengurangi waktu pengembangan untuk aplikasi Universal.